Openssl Generate Private Key As Pe
Posted : admin On 12.04.2020Oct 15, 2015 Download latest Far Cry Primal product cd key generator and generate your own free activation cd key. Redeem your generated product code and play this game online today!! Our team share to you the fresh and updated keygen. We decide to create this key generator to enable fellow gamers to grab a free CD key. Far Cry Primal Code Generator. Our accomplices routinely offers us an extensive number of free initiation keys which enables us to offer you free permit key each day through Far Cry Primal code generator device.Far Cry Primal CD KEY or Product Key is essential. The respect winning Far Cry Primal 2020 Activation Key foundation that smoldered the tropics and the Himalayas right as of now enters the essential fight for mankind’s survival with its innovative open-world sandbox steady correspondence, joining huge mammoths, dazzling. Far cry primal activation key generator. Apr 09, 2020 Far Cry Primal 2020 Crack & Activation Key PC Game Free Download. The regard winning Far Cry Primal 2020 Crack establishment that fumed the tropics and the Himalayas right presently enters the fundamental battle for humanity’s survival with its. About Far Cry Primal Keygen and Key Generator Features. Far Cry Primal Keygen took us a good amount of time to develop, mainly because cracking the codes wasn’t all that easy. Now that we have finally finished the Far Cry Primal Keygen we are proudly.
This article discusses how to generate an unencrypted private key and public certificate pair that is suitable for use with HTTPS, FTPS, and the administrative port for EFT Server. (To generate an encrypted key/certificate pair, refer to Generating an Encrypted Private Key and Self-Signed Public Certificate.) General Information. In this case, you can generate a new self-signed certificate that represents a Common Name your application can validate. This topic tells you how to generate self-signed SSL certificate requests using the OpenSSL toolkit to enable HTTPS connections. Run the following OpenSSL command to generate your private key and public certificate. This module allows one to (re)generate OpenSSL private keys. Axure 9 license. One can generate RSA, DSA, ECC or EdDSA private keys. Keys are generated in PEM format. Please note that the module regenerates private keys if they don’t match the module’s options. In particular, if you provide another passphrase (or specify none), change the keysize, etc., the private key will be regenerated. This module allows one to (re)generate OpenSSL private keys. One can generate RSA, DSA, ECC or EdDSA private keys. Keys are generated in PEM format. Please note that the module regenerates private keys if they don’t match the module’s options. OpenSSL in Linux is the easiest way to decrypt an encrypted private key. Use the following command to decrypt an encrypted RSA key: Make sure to replace the “server.key.secure” with the filename of your encrypted key, and “server.key” with the file name that you want for your encrypted output key file. Generating private keys with openssl Keys are the basis of public key algorithms and PKI. Keys usually come in pairs, with one half being the public key and the other half being the private key. With OpenSSL, the private key contains the public key information as well, so a public key doesn’t need to be generated separately. Common OpenSSL Commands with Keys and Certificates. Generate RSA private key with certificate in a single command openssl req -x509 -newkey rsa:4096 -sha256 -keyout example.key -out example.crt -subj '/CN=example.com' -days 3650 -passout pass:foobar.
- Openssl Generate Private Key As Pe Server
- Openssl Create Private Key Pem
- Advantages Of Private Key Encryption
- Openssl Generate Private Key As Penn State
Common OpenSSL Commands with Keys and Certificates
Generate RSA private key with certificate in a single command
Generate Certificate Signing Request (CSR) from private key with passphrase
Generate RSA private key (2048 bit)
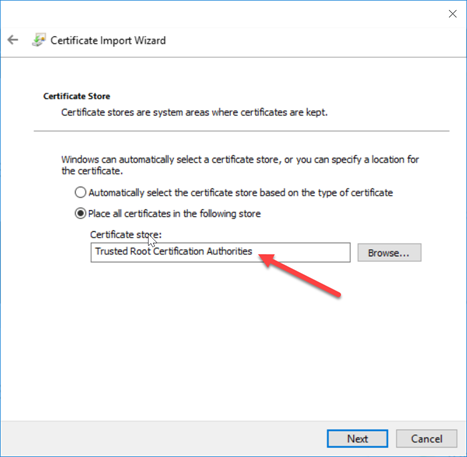
Generate a Certificate Signing Request (CSR)
Generate RSA private key (2048 bit) and a Certificate Signing Request (CSR) with a single command
Convert private key to PEM format
Generate a self-signed certificate that is valid for a year with sha256 hash
Openssl Generate Private Key As Pe Server
View details of a RSA private key
View details of a CSR
View details of a Certificate
View details of a Certificate in DER format
Openssl Create Private Key Pem
Convert a DER file (.crt .cer .der) to PEM
Advantages Of Private Key Encryption
Convert a PEM file to DER
| # Define where to store the generated certs and metadata. |
| DIR='$(pwd)/tls' |
| # Optional: Ensure the target directory exists and is empty. |
| rm -rf '${DIR}' |
| mkdir -p '${DIR}' |
| # Create the openssl configuration file. This is used for both generating |
| # the certificate as well as for specifying the extensions. It aims in favor |
| # of automation, so the DN is encoding and not prompted. |
| cat >'${DIR}/openssl.cnf'<<EOF |
| [req] |
| default_bits = 2048 |
| encrypt_key = no # Change to encrypt the private key using des3 or similar |
| default_md = sha256 |
| prompt = no |
| utf8 = yes |
| # Speify the DN here so we aren't prompted (along with prompt = no above). |
| distinguished_name = req_distinguished_name |
| # Extensions for SAN IP and SAN DNS |
| req_extensions = v3_req |
| # Be sure to update the subject to match your organization. |
| [req_distinguished_name] |
| C = US |
| ST = California |
| L = The Cloud |
| O = Demo |
| CN = My Certificate |
| # Allow client and server auth. You may want to only allow server auth. |
| # Link to SAN names. |
| [v3_req] |
| basicConstraints = CA:FALSE |
| subjectKeyIdentifier = hash |
| keyUsage = digitalSignature, keyEncipherment |
| extendedKeyUsage = clientAuth, serverAuth |
| subjectAltName = @alt_names |
| # Alternative names are specified as IP.# and DNS.# for IP addresses and |
| # DNS accordingly. |
| [alt_names] |
| IP.1 = 1.2.3.4 |
| DNS.1 = my.dns.name |
| EOF |
| # Create the certificate authority (CA). This will be a self-signed CA, and this |
| # command generates both the private key and the certificate. You may want to |
| # adjust the number of bits (4096 is a bit more secure, but not supported in all |
| # places at the time of this publication). |
| # |
| # To put a password on the key, remove the -nodes option. |
| # |
| # Be sure to update the subject to match your organization. |
| openssl req |
| -new |
| -newkey rsa:2048 |
| -days 120 |
| -nodes |
| -x509 |
| -subj '/C=US/ST=California/L=The Cloud/O=My Company CA' |
| -keyout '${DIR}/ca.key' |
| -out '${DIR}/ca.crt' |
| # |
| # For each server/service you want to secure with your CA, repeat the |
| # following steps: |
| # |
| # Generate the private key for the service. Again, you may want to increase |
| # the bits to 4096. |
| openssl genrsa -out '${DIR}/my-service.key' 2048 |
| # Generate a CSR using the configuration and the key just generated. We will |
| # give this CSR to our CA to sign. |
| openssl req |
| -new -key '${DIR}/my-service.key' |
| -out '${DIR}/my-service.csr' |
| -config '${DIR}/openssl.cnf' |
| # Sign the CSR with our CA. This will generate a new certificate that is signed |
| # by our CA. |
| openssl x509 |
| -req |
| -days 120 |
| -in '${DIR}/my-service.csr' |
| -CA '${DIR}/ca.crt' |
| -CAkey '${DIR}/ca.key' |
| -CAcreateserial |
| -extensions v3_req |
| -extfile '${DIR}/openssl.cnf' |
| -out '${DIR}/my-service.crt' |
| # (Optional) Verify the certificate. |
| openssl x509 -in '${DIR}/my-service.crt' -noout -text |
| # Here is a sample response (truncate): |
| # |
| # Certificate: |
| # Signature Algorithm: sha256WithRSAEncryption |
| # Issuer: C = US, ST = California, L = The Cloud, O = My Organization CA |
| # Subject: C = US, ST = California, L = The Cloud, O = Demo, CN = My Certificate |
| # # .. |
| # X509v3 extensions: |
| # X509v3 Basic Constraints: |
| # CA:FALSE |
| # X509v3 Subject Key Identifier: |
| # 36:7E:F0:3D:93:C6:ED:02:22:A9:3D:FF:18:B6:63:5F:20:52:6E:2E |
| # X509v3 Key Usage: |
| # Digital Signature, Key Encipherment |
| # X509v3 Extended Key Usage: |
| # TLS Web Client Authentication, TLS Web Server Authentication |
| # X509v3 Subject Alternative Name: |
| # IP Address:1.2.3.4, DNS:my.dns.name |
| # |